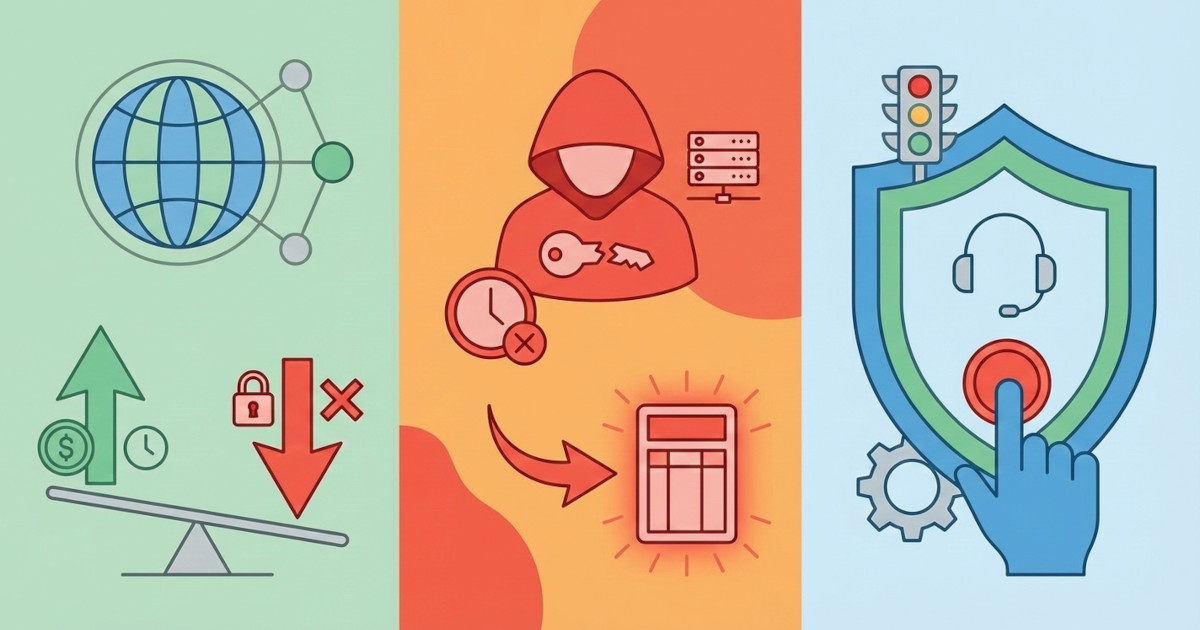
Corporate cards have rebates and payment terms that mobile schemes can't match directly. The winning strategy targets vertical wedges where cards structurally fail starting with fleet EV transition and healthcare payouts.
We can't find the internet
Attempting to reconnect
Something went wrong!
Hang in there while we get back on track
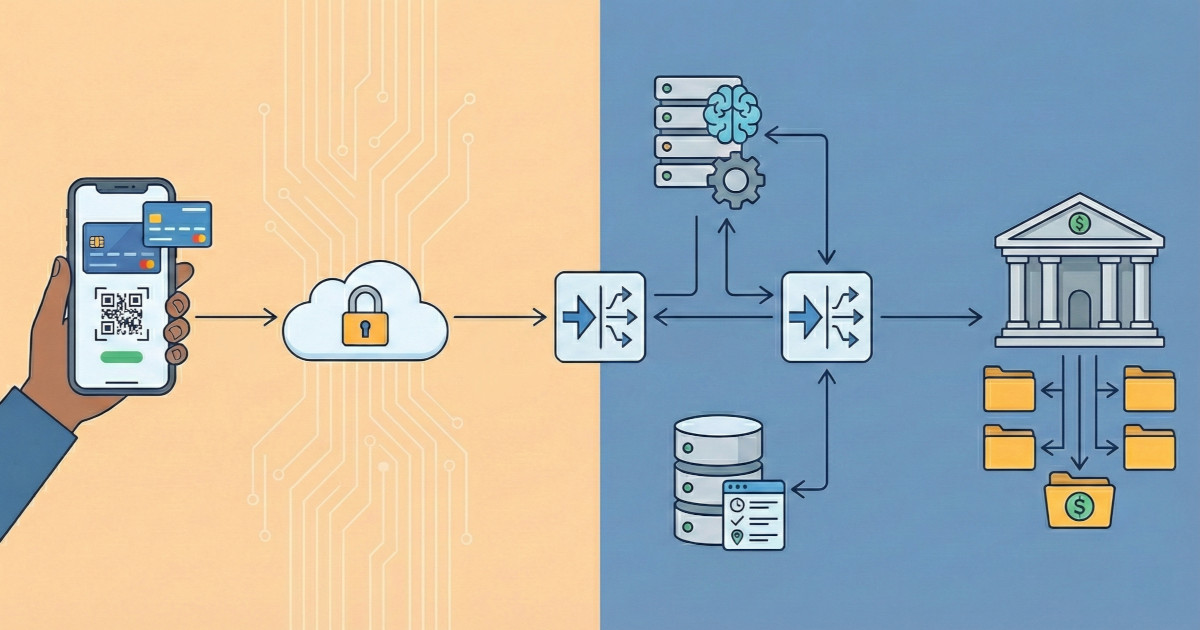
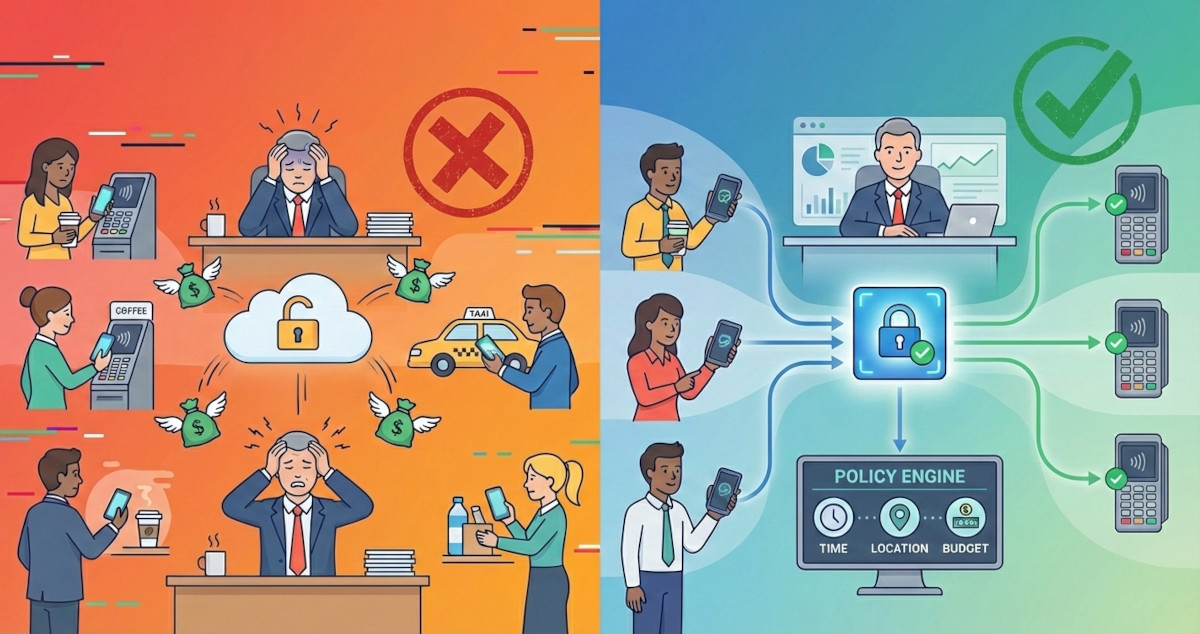
Adding decision points to payments schemes requires careful architecture. Sub-accounts, security, latency budgets: this post covers the technical design for corporate authorization approvals that works in production.
Corporate B2B payments represent massive guaranteed transaction volume, but mobile payment schemes are locked out. The reason isn't merchant acceptance or user experience: it's the lack of spending controls. Learn why CFOs won't adopt mobile wallets for corporate expenses without pre-payment authorization.
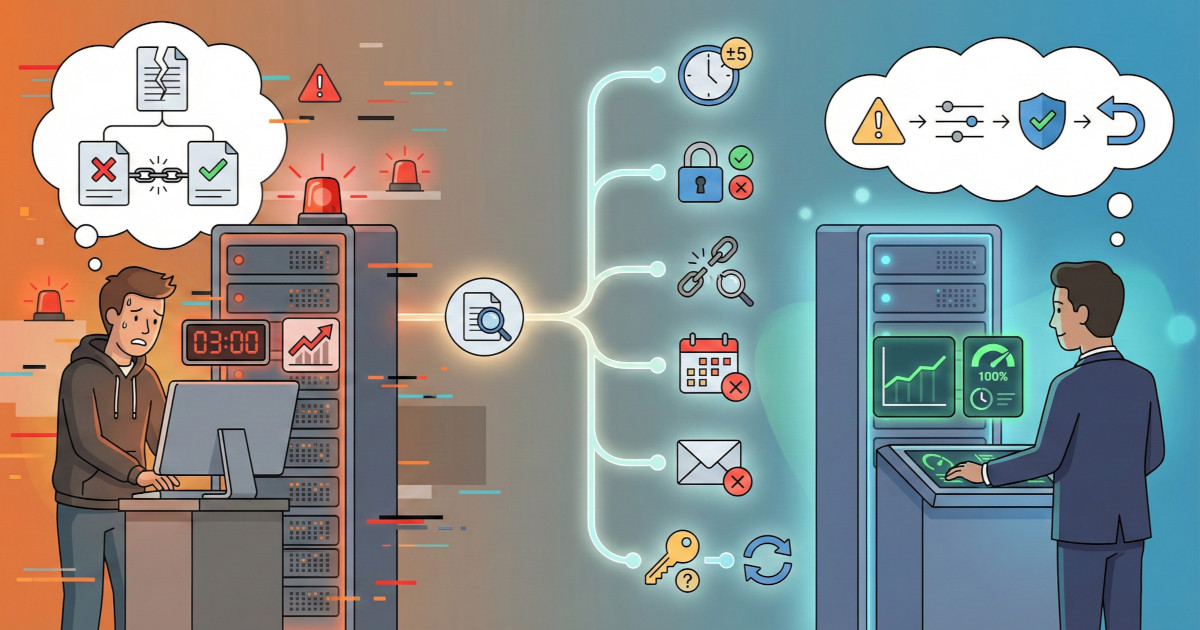
The difference between toy implementations and production systems is operational discipline. Let's discuss critical test cases (including the failures everyone forgets), phased migration strategies that won't break production, contract testing with partners, and a complete troubleshooting guide for when signatures fail in the middle of the night, common issues, and when to escalate to partners.
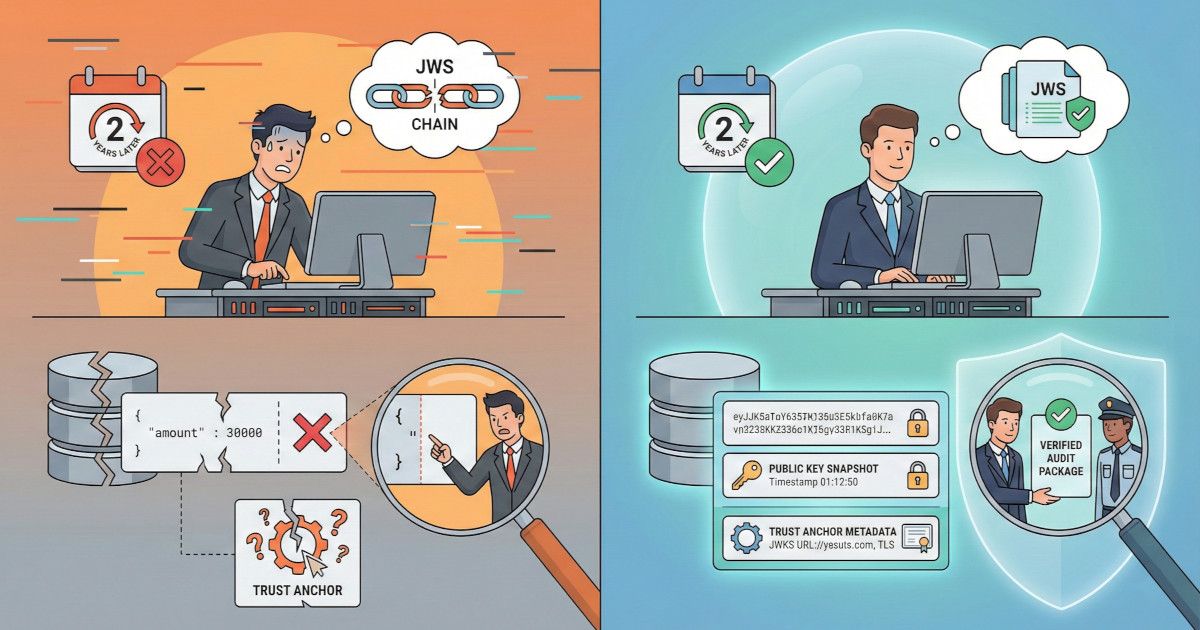
Non-repudiation isn't just about signing requests, it's about preserving proof that survives years, disputes, and regulatory audits. Let's go over what to store (original JWS string, public keys, verification metadata), how to avoid canonicalization traps, implementing replay attack prevention, and building a complete dispute resolution playbook.
A partner's JWKS endpoint goes down for 2 hours due to DNS issues. Do you reject €300K in legitimate transactions, or keep using cached keys and risk accepting fraudulent signatures if this is actually a compound attack? Learn how to build production-grade JWKS for 200+ partners, implement stale-while-revalidate caching with security safeguards, and create human-in-the-loop verification for potential incidents. Get the operational runbooks for systems handling irreversible transactions.
Your former employee with key access just left on bad terms. Your runbook says key rotation will take 6-12 hours coordinating with 50+ partner banks—while the compromised key stays active in production processing real money. JWKS (JSON Web Key Set) transforms this nightmare into a 5-minute configuration change by publishing keys at a standard endpoint that clients fetch automatically. Learn the four-phase rotation process that achieves zero downtime, why the kid is critical, and the caching strategies that make JWKS performant at scale.
Signature verification is expensive, and attackers can exploit this. This post explains why JWS alone isn't enough for authentication, how Open Banking's three-layer architecture (mTLS, OAuth, JWS) prevents signature-based DoS attacks, and the fundamental principle: expensive operations must be protected by cheap gates. Short but critical for production security.
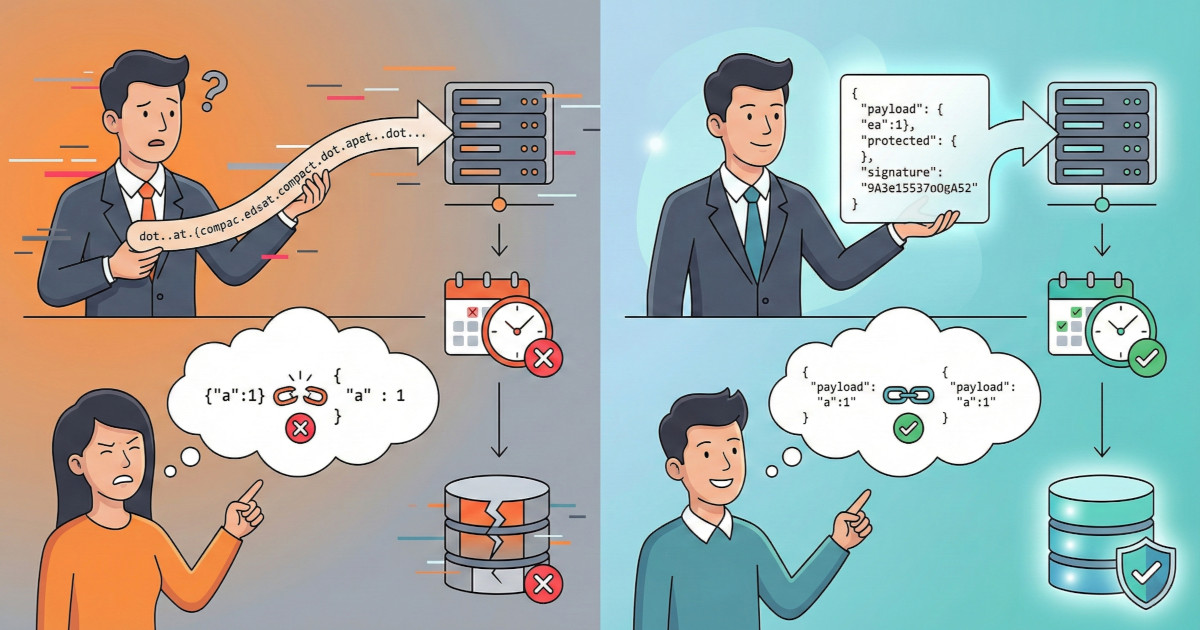
Algorithm choice isn't academic: it determines whether your signatures survive security audits and legal challenges. This post decodes algorithm names (RS256, ES384, EdDSA), explains the security properties of each family (HMAC, RSA, ECDSA), covers known attacks like the Sony PS3 hack and Bitcoin wallet thefts, and provides a decision framework that balances technical merit with organizational reality.
Theory is nice, but you need working code. Follow along as we build a complete Elixir and JOSE implementation for signing and verifying payment instructions with ES256, including a production-ready Phoenix Plug. Learn critical decisions like compact vs flattened JSON serialization, how to handle clock skew tolerance, and the canonicalization traps that will break your signatures if you're not careful.